Exempting VPN traffic from NAT [ Notes to self series ]
Welcome
Hey, welcome! This is just a little “notes to self” series. Nothing fancy, just me writing down what I’ve learned from solving stuff. It’s kinda different from the usual things I post. Aha! I solved it. That rush of dopamine hitting my system, screaming, “I finally solved it!”
Discussion with myself 😀
So, for my project, I needed to set up a VPN in Cisco Packet Tracer. But the issue was how? It seemed really difficult at first. Because people said that for the VPN to work, you need to make sure that the VPN ( Virtual Private Network ) traffic should be exempted from NAT ( Network Address Translation )
Using this in mind, I tried various ways. I watched countless videos and tutorials, but I got even more confused. Because my VPN wasn't working.
So I decided to start over and rewatch the VPN basics to carefully understand how everything works. Because I was determined to solve this badly.
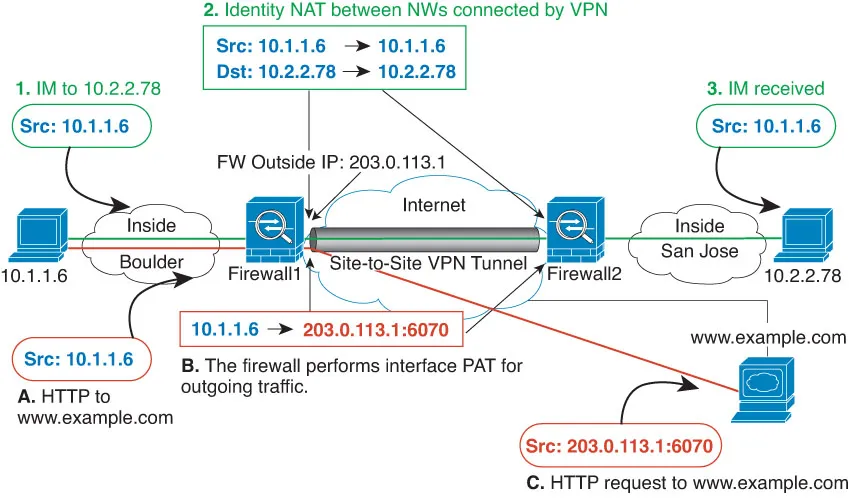
Source: Defense Orchestrator Docs - NAT and Site-to-Site VPN
Do not take the image above seriously... I’m just using it to show something similar to what I had for my project, haha.
Then, after thinking and trying, I finally found out my solution.
It was ...
THE ACCESS CONTROL LIST
And this small detail changes everything. It's about how the access control list is ORDERED. Because the access list processes from TOP to BOTTOM.
For the NAT access control list, make sure to place DENY first. For example, deny ip. And then apply the rules that permits IPs to be NATed, permit ip.
This is to prevent the IPs that are used in VPN to prevent it from being NATed. It does not make sense for it to be NATed. After all, VPN is private, and it does not really need to be translated into a public address.
Generally, VPN traffic does not need to be NATed because it needs to maintain its original IP address. Before it establishes the tunnel and encrypts it properly.
This is an example :
⚠️ Fake IP
Define the NAT pool public addresses.
ip nat pool PUBLIC_POOL 198.51.100.10 198.51.100.20 netmask 255.255.255.0
Now, define the access list to control the NAT. In this case, make sure to deny IPs that are used for VPN traffic. Before permitting NATed traffic.
ip access-list extended NAT_ACL
deny ip 192.168.1.0 0.0.0.255 10.10.0.0 0.0.255.255
permit ip 192.168.1.0 0.0.0.255 any
Then apply NAT to the interfaces inside using NAT_ACL access list
ip nat inside source list NAT_ACL pool PUBLIC_POOL overload
Thanks for listening to my ramblings.🍰
Signing off,
noob3Int 🤩