Cool Recon Tools
Hello and welcome to my blog. Today, we will be seeing some cool recon tools that are very fun and not time consuming to use. Some of this tool are usually used during my day to day pentest and sometimes when I am bored I usually use this tools as I am trying to learn about bug bounty now when I have the time.
This tool contains a lot of things, ranging from viewing sensitive files to checking Wayback URLs. It's a website that collects all recon tools in one place. Anyone can use it, and it's completely free

FOFA is a search query that lets you discover and map internet-connected devices, services, and infrastructure which is similar to Shodan, it helps you find exposed systems, specific technologies, or vulnerabilities across the web.
For FOFA, the syntax is different from google dorking. Maybe in another blog, I will show what cool FOFA queries we can use in order to see stuff on our target 😉
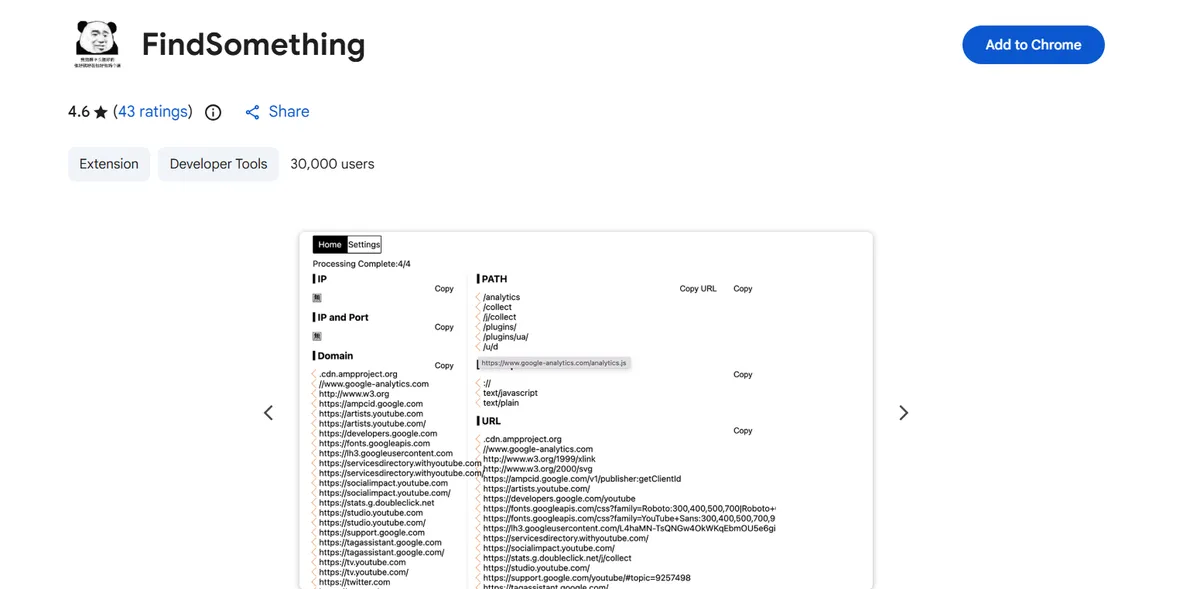
I just have to say, I LOVE this extension. It has helped me uncover so many hidden directories that brute forcing and wordlists completely missed. I use this extension every time. It is just one of my favorite tool and a must have that has blend in into my methodology.
This tool extract interesting and juicy information from the HTML source code and the javascript files. It is free to use as well !
This is another site that I love, this site uses some of the creators custom dorks that are creative that I usually use ! Highly recommend 😉
This is one of the recent tools I saw. I heard so many good things about it like how it can collect tons of domains without needing API keys from platforms like Shodan and others. And I can safely say, when I ran it on one of my targets, it pulled up a whole list of them haha.
Below, I will walk you through how I use it, but I'm sticking with my own domain for this demo. Don't want to accidentally pick the wrong target and land myself in hot water 🤭
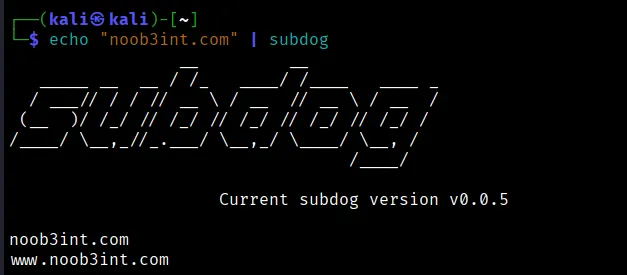
The syntax is super straightforward. Just run the command below and you are good to go
echo "<target>" | subdog
But of course do take note, the subdomains that you may get from this may be false positive and it is important to double check with tools like httpx to confirm if the domain is alive.
This is another cool tool that's used to brute-force AWS buckets and check if there are any buckets open to the internet that allow anonymous access. This tool is from NahamSec, who I really look up to because he makes tons of bug bounty videos (HIGHLY RECOMMEND CHECKING HIM OUT).
The syntax is straightforward here too. Just be ready to wait a bit as this proccess cycles through 9013 different word combinations to find open AWS buckets.
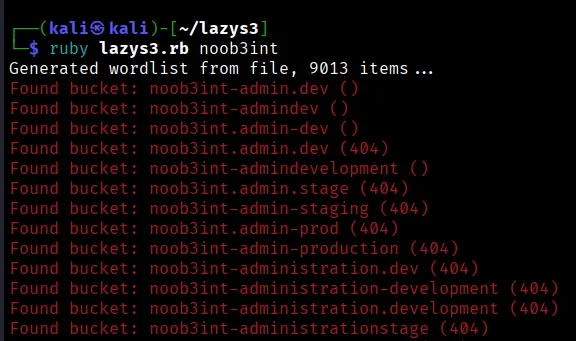
The syntax for this is :
ruby lazys3.rb <target>
That is all for today! I hope this cool recon tools help you with your pentest and bug bounty hunt !
That is all, folks! I hope these tools can help you with your bug bounty hunting and pentesting to uncover even more hidden vulnerabilities! Thank you for reading!😸

Signing off,
Noob3int 📞